概述 本章節主要介紹配置HaProxy+Keepalived高可用群集,Mycat的配置就不在這裡做介紹,可以參考我前面寫的幾篇關於Mycat的文章。 部署圖: 配置 HaProxy安裝 181和179兩台伺服器安裝haproxy的步驟一致 --創建haproxy用戶 useradd haproxy
概述
本章節主要介紹配置HaProxy+Keepalived高可用群集,Mycat的配置就不在這裡做介紹,可以參考我前面寫的幾篇關於Mycat的文章。
部署圖:

配置
HaProxy安裝
181和179兩台伺服器安裝haproxy的步驟一致
--創建haproxy用戶 useradd haproxy --解壓完後進入haproxy目錄 cd haproxy-1.4.25/ --編譯安裝 make TARGET=linux26 PREFIX=/usr/local/haproxy ARCH=x86_64 make install PREFIX=/usr/local/haproxy
HaProxy配置
cd /usr/local/haproxy
touch haproxy.cfg
vim haproxy.cfg
global
log 127.0.0.1 local0 ##記日誌的功能
maxconn 4096
chroot /usr/local/haproxy
user haproxy
group haproxy
daemon
defaults
log global
option dontlognull
retries 3
option redispatch
maxconn 2000
contimeout 5000
clitimeout 50000
srvtimeout 50000
listen admin_stats 192.168.57.180:48800
stats uri /admin-status ##統計頁面
stats auth admin:admin
mode http
option httplog
listen allmycat_service 192.168.57.180:8098
mode tcp
option tcplog
option httpchk OPTIONS * HTTP/1.1\r\nHost:\ www
balance roundrobin
server mycat_181 192.168.57.181:8066 check port 48700 inter 5s rise 2 fall 3
server mycat_179 192.168.57.179:8066 check port 48700 inter 5s rise 2 fall 3
srvtimeout 20000
配置haproxy記錄日誌功能
yum –y install rsyslog
mkdir /etc/rsyslog.d
cd /etc/rsyslog.d/
touch haproxy.conf
vim haproxy.conf
$ModLoad imudp $UDPServerRun 514 local0.* /var/log/haproxy.log
vim /etc/rsyslog.conf
在#### RULES ####上面一行加入以下內容
# Include all config files in /etc/rsyslog.d/ $IncludeConfig /etc/rsyslog.d/*.conf

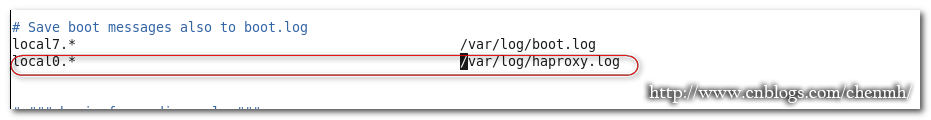
在local7.* /var/log/boot.log下麵加入以下內容
local0.* /var/log/haproxy.log
重啟rsyslog服務
service rsyslog restart
將rsyslog加入自動啟動服務
chkconfig --add rsyslog chkconfig --level 2345 rsyslog on
配置監聽mycat是否存活
安裝xinetd插件
yum install xinetd -y
cd /etc/xinetd.d touch mycat_status
vim mycat_status
service mycat_status { flags = REUSE socket_type = stream port = 48700 wait = no user = nobody server =/usr/local/bin/mycat_status log_on_failure += USERID disable = no }
創建xinetd啟動服務腳本
vim /usr/local/bin/mycat_status
#!/bin/bash #/usr/local/bin/mycat_status.sh # This script checks if a mycat server is healthy running on localhost. It will # return: # # "HTTP/1.x 200 OK\r" (if mycat is running smoothly) # # "HTTP/1.x 503 Internal Server Error\r" (else) mycat=`/usr/local/mycat/bin/mycat status |grep 'not running'| wc -l` if [ "$mycat" = "0" ]; then /bin/echo -e "HTTP/1.1 200 OK\r\n" else /bin/echo -e "HTTP/1.1 503 Service Unavailable\r\n" fi
修改腳本文件許可權
我就是在這裡被坑了很久,根據權威指南上面mycat_status這個腳本裡面的內容也有很多問題,好幾個地方沒有空格.
chmod 777 /usr/local/bin/mycat_status chmod 777 /etc/xinetd.d/mycat_status
將啟動腳本加入服務
vim /etc/services
在末尾加入
mycat_status 48700/tcp # mycat_status
重啟xinetd服務
service xinetd restart
將xinetd加入自啟動服務
chkconfig --add xinetd chkconfig --level 2345 xinetd on
頁面測試
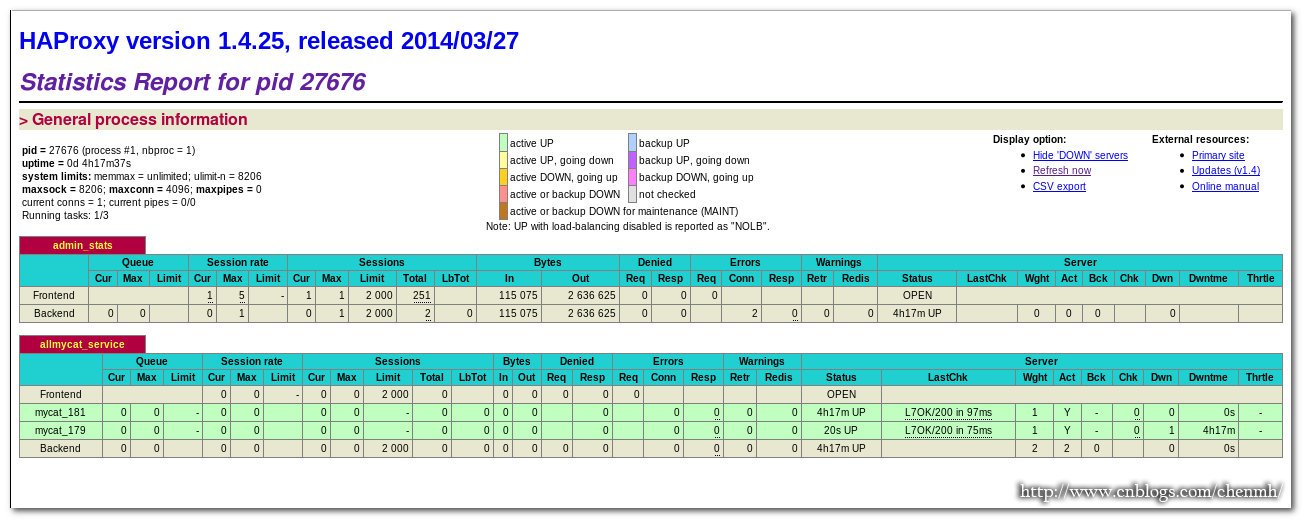
http://192.168.57.180:48800/admin-status

由於179還沒有安裝好,所以這裡179顯示連接失敗
創建haproxy啟停腳本
啟動腳本
touch /usr/local/haproxy/sbin/start chmod +x /usr/local/haproxy/sbin/start vim /usr/local/haproxy/sbin/start
#!/bin/sh /usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/haproxy.cfg &
關閉腳本
touch /usr/local/haproxy/sbin/stop chmod +x /usr/local/haproxy/sbin/stop vim /usr/local/haproxy/sbin/stop
#!/bin/sh ps -ef | grep sbin/haproxy | grep -v grep |awk '{print $2}'|xargs kill -s 9
授權
chown -R haproxy.haproxy /usr/local/haproxy/*
Keepalived安裝步驟
keepalived的安裝步驟過程在兩台伺服器上除了keepalived.conf配置文件稍微有點區別外其他的地方都一致。
openssl安裝
./config --prefix=/usr/local/openssl ./config -t make depend make make test make install ln -s /usr/local/openssl /usr/local/ssl vim /etc/ld.so.conf
在文件末尾加入以下內容
/usr/local/openssl/lib
修改環境變數
vim /etc/profile
在文件末尾加入以下內容
export OPENSSL=/usr/local/openssl/bin export PATH=$PATH:$OPENSSL
使環境變數立刻生效
source /etc/profile
安裝openssl-devel
yum install openssl-devel -y
測試
ldd /usr/local/openssl/bin/openssl
linux-vdso.so.1 => (0x00007fff996b9000) libdl.so.2 =>/lib64/libdl.so.2 (0x00000030efc00000) libc.so.6 =>/lib64/libc.so.6 (0x00000030f0000000) /lib64/ld-linux-x86-64.so.2 (0x00000030ef800000)
which openssl
/usr/bin/openssl
openssl version
OpenSSL 1.0.0-fips 29 Mar 2010
keepalived安裝
./configure --prefix=/usr/local/keepalived make make install cp /usr/local/keepalived/sbin/keepalived /usr/sbin/ cp /usr/local/keepalived/etc/sysconfig/keepalived /etc/sysconfig/ cp /usr/local/keepalived/etc/rc.d/init.d/keepalived /etc/init.d/ mkdir /etc/keepalived cd /etc/keepalived/ cp /usr/local/keepalived/etc/keepalived/keepalived.conf /etc/keepalived mkdir -p /usr/local/keepalived/var/log
創建配置文件和腳本
mkdir /etc/keepalived/scripts
cd /etc/keepalived/scripts
vim /etc/keepalived/keepalived.conf
master
! Configuration Fileforkeepalived vrrp_script chk_http_port { script"/etc/keepalived/scripts/check_haproxy.sh" interval 2 weight 2 } vrrp_instance VI_1 { state MASTER #192.168.57.179上改為BACKUP interface eth0 #對外提供服務的網路介面 virtual_router_id 51 #VRRP組名,兩個節點的設置必須一樣,以指明各個節點屬於同一VRRP組 priority 150 #數值愈大,優先順序越高,backup上改為120 advert_int 1 #同步通知間隔 authentication { #包含驗證類型和驗證密碼。類型主要有PASS、AH兩種,通常使用的類型為PASS,據說AH使用時有問題 auth_type PASS auth_pass 1111 } track_script { chk_http_port #調用腳本check_haproxy.sh檢查haproxy是否存活 } virtual_ipaddress { #vip地址,這個ip必須與我們在lvs客戶端設定的vip相一致 192.168.57.180 dev eth0 scope global } notify_master /etc/keepalived/scripts/haproxy_master.sh notify_backup /etc/keepalived/scripts/haproxy_backup.sh notify_fault /etc/keepalived/scripts/haproxy_fault.sh notify_stop /etc/keepalived/scripts/haproxy_stop.sh }
backup
! Configuration Fileforkeepalived vrrp_script chk_http_port { script"/etc/keepalived/scripts/check_haproxy.sh" interval 2 weight 2 } vrrp_instance VI_1 { state BACKUP #192.168.57.179上改為BACKUP interface eth0 #對外提供服務的網路介面 virtual_router_id 51 #VRRP組名,兩個節點的設置必須一樣,以指明各個節點屬於同一VRRP組 priority 120 #數值愈大,優先順序越高,backup上改為120 advert_int 1 #同步通知間隔 authentication { #包含驗證類型和驗證密碼。類型主要有PASS、AH兩種,通常使用的類型為PASS,據說AH使用時有問題 auth_type PASS auth_pass 1111 } track_script { chk_http_port #調用腳本check_haproxy.sh檢查haproxy是否存活 } virtual_ipaddress { #vip地址,這個ip必須與我們在lvs客戶端設定的vip相一致 192.168.57.180 dev eth0 scope global } notify_master /etc/keepalived/scripts/haproxy_master.sh notify_backup /etc/keepalived/scripts/haproxy_backup.sh notify_fault /etc/keepalived/scripts/haproxy_fault.sh notify_stop /etc/keepalived/scripts/haproxy_stop.sh }
vim /etc/keepalived/scripts/check_haproxy.sh
#!/bin/bash STARTHAPROXY="/usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/haproxy.cfg" STOPKEEPALIVED="/etc/init.d/keepalived stop" LOGFILE="/usr/local/keepalived/var/log/keepalived-haproxy-state.log" echo "[check_haproxy status]" >> $LOGFILE A=`ps -C haproxy --no-header |wc -l` echo "[check_haproxy status]" >> $LOGFILE date >> $LOGFILE if [ $A -eq 0 ];then echo $STARTHAPROXY >> $LOGFILE $STARTHAPROXY >> $LOGFILE 2>&1 sleep 5 fi if [ `ps -C haproxy --no-header |wc -l` -eq 0 ];then exit 0 else exit 1 fi
vim /etc/keepalived/scripts/haproxy_master.sh
#!/bin/bash STARTHAPROXY=`/usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/haproxy.cfg`
STOPHAPROXY=`ps -ef | grep sbin/haproxy | grep -v grep | awk '{print $2}'| xargs kill -s 9` LOGFILE="/usr/local/keepalived/var/log/keepalived-haproxy-state.log" echo "[master]" >> $LOGFILE date >> $LOGFILE echo "Being master...." >> $LOGFILE 2>&1 echo "stop haproxy...." >> $LOGFILE 2>&1 $STOPHAPROXY >> $LOGFILE 2>&1 echo "start haproxy...." >> $LOGFILE 2>&1 $STARTHAPROXY >> $LOGFILE 2>&1 echo "haproxy stared ..." >> $LOGFILE
vim /etc/keepalived/scripts/haproxy_backup.sh
#!/bin/bash STARTHAPROXY=`/usr/local/haproxy/sbin/haproxy -f /usr/local/haproxy/haproxy.cfg` STOPHAPROXY=`ps -ef | grep sbin/haproxy | grep -v grep | awk '{print $2}'| xargs kill -s 9` LOGFILE="/usr/local/keepalived/var/log/keepalived-haproxy-state.log" echo "[backup]" >> $LOGFILE date >> $LOGFILE echo "Being backup...." >> $LOGFILE 2>&1 echo "stop haproxy...." >> $LOGFILE 2>&1 $STOPHAPROXY >> $LOGFILE 2>&1 echo "start haproxy...." >> $LOGFILE 2>&1 $STARTHAPROXY >> $LOGFILE 2>&1 echo "haproxy stared ..." >> $LOGFILE
vim /etc/keepalived/scripts/haproxy_fault.sh
#!/bin/bash LOGFILE=/usr/local/keepalived/var/log/keepalived-haproxy-state.log echo "[fault]" >> $LOGFILE date >> $LOGFILE
vim /etc/keepalived/scripts/haproxy_stop.sh
#!/bin/bash LOGFILE=/usr/local/keepalived/var/log/keepalived-haproxy-state.log echo "[stop]" >> $LOGFILE date >> $LOGFILE
賦予腳本可執行許可權
chmod 777 /etc/keepalived/scripts/*
將keepalived加入自啟動服務
chkconfig --add keepalived chkconfig --level 2345 keepalived on --啟動服務 service keepalived start
總結
權威指南上面代碼部分好多處都存在問題,幾乎每一塊代碼都存在問題,有時候往往一個空格需要花很長的時間去找這個問題,所以在代碼方面要細心;特別是複製別人的代碼不要原本照抄最好是檢查一下,除了代碼本身的問題許可權有時候也是容易忽略的錯誤,特別是可執行文件要註意是否有可執行許可權。
|
備註: 作者:pursuer.chen 博客:http://www.cnblogs.com/chenmh 本站點所有隨筆都是原創,歡迎大家轉載;但轉載時必須註明文章來源,且在文章開頭明顯處給明鏈接。 《歡迎交流討論》 |



