1、httpd簡介? http是Apache超文本傳輸協議伺服器的主程式。它是一個獨立的後臺進程,能夠處理請求的子進程和線程。 http常用用的兩個版本是httpd-2.2和httpd-2.4 CentOS6系列的預設httpd版本是httpd-2.2版本的rpm包 CentOS7系列的預設http ...
目錄
1、httpd簡介?
http是Apache超文本傳輸協議伺服器的主程式。它是一個獨立的後臺進程,能夠處理請求的子進程和線程。
http常用用的兩個版本是httpd-2.2和httpd-2.4
- CentOS6系列的預設httpd版本是httpd-2.2版本的rpm包
- CentOS7系列的預設httpd版本是httpd-2.4版本的rpm包
2、httpd服務特點
| 名稱 | 特點 |
|---|---|
| 高度模塊化 | core + modules,核心加模塊,想要什麼功能添加什麼模塊; |
| DSO | Dynamic Shared Object,動態共用庫; |
| MPM | Multipath processing Modules 多路處理模塊。 |
3、 httpd的工作模型
- prefork:兩級進程模型,父進程管理子進程,每個進程響應一個請求
# 工作模型
一個主進程:
負責生成子進程及回收子進程
負責創建套接字、接受請求,並將其派發給某子進程進行處理
n個子進程:
每個子進程處理一個請求
# 註意:
會預先生成幾個空閑進程,隨時等待用於響應用戶請求,最大不會超過1024個
- worker:三級進程模型,父進程管理子進程,子進程通過線程響應用戶請求,每個線程處理一個用戶請求
# 工作模型
一個主進程:
負責生成子進程、創建套接字、接受請求,並將其派發給某子進程進行處理
多個子進程:
每個子進程負責生成多個線程
每個線程:
負責響應用戶請求
- event:兩級模型,父進程管理子進程,子進程通過事件驅動event-driven機制直接響應n個請求
# 工作模型:
一個主進程:
負責生成子進程、創建套接字、接受請求,並將其派發給某子進程進行處理
子進程:
基於事件驅動機制直接響應多個請求
4、httpd的配置文件
| 文件/目錄 | 對應的功能 |
|---|---|
| /var/log/httpd/access.log | 訪問日誌 |
| /var/log/httpd/error_log | 錯誤日誌 |
| /var/www/html/ | 站點文檔目錄 |
| /usr/lib64/httpd/modules/ | 模塊文件路徑 |
| /etc/httpd/conf/httpd.conf | 主配置文件 |
| /etc/httpd/conf.modules.d/*.conf | 模塊配置文件 |
| /etc/httpd/conf.d/*.conf | 輔助配置文件 |
5、httpd自帶的工具程式
| 工具 | 功能 |
|---|---|
| htpasswd | basic認證基於文件實現時,用到的帳號密碼生成工具 |
| apachectl | httpd自帶的服務控制腳本,支持start,stop,restart |
| apxs | 由httpd-devel包提供的,擴展httpd使用第三方模塊的工具 |
| rotatelogs | 日誌滾動工具 |
| suexec | 訪問某些有特殊許可權配置的資源時,臨時切換至指定用戶運行的工具 |
| ab | apache benchmark,httpd的壓力測試工具 |
6、httpd常用配置
6.1 安裝httpd服務
[root@localhost ~]# dnf install -y httpd //用dnf安裝httpd服務
[root@localhost ~]# systemctl status httpd //服務預設是未開啟的
● httpd.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; disabled; vendor pres>
Active: inactive (dead)
Docs: man:httpd.service(8)
[root@localhost ~]# systemctl stop firewalld //開啟服務前關閉防火牆
[root@localhost ~]# systemctl start httpd //開啟httpd服務
[root@localhost ~]# systemctl status httpd //查看服務是否開啟成功
● httpd.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; disabled; vendor pres>
Active: active (running) since Thu 2022-07-21 21:16:35 CST; 14s ago
Docs: man:httpd.service(8)
Main PID: 15207 (httpd)
Status: "Running, listening on: port 80"
Tasks: 213 (limit: 11202)
Memory: 24.8M
CGroup: /system.slice/httpd.service
├─15207 /usr/sbin/httpd -DFOREGROUND
├─15208 /usr/sbin/httpd -DFOREGROUND
├─15209 /usr/sbin/httpd -DFOREGROUND
├─15210 /usr/sbin/httpd -DFOREGROUND
└─15211 /usr/sbin/httpd -DFOREGROUND
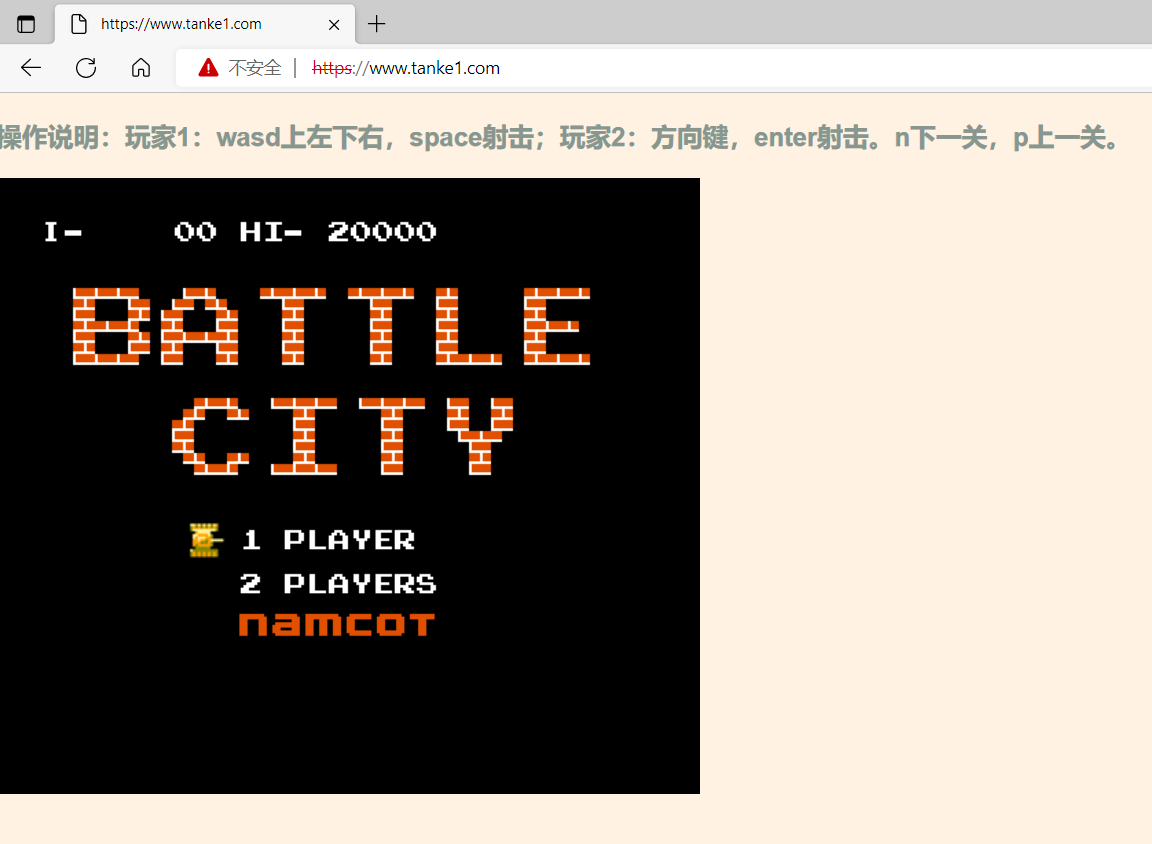
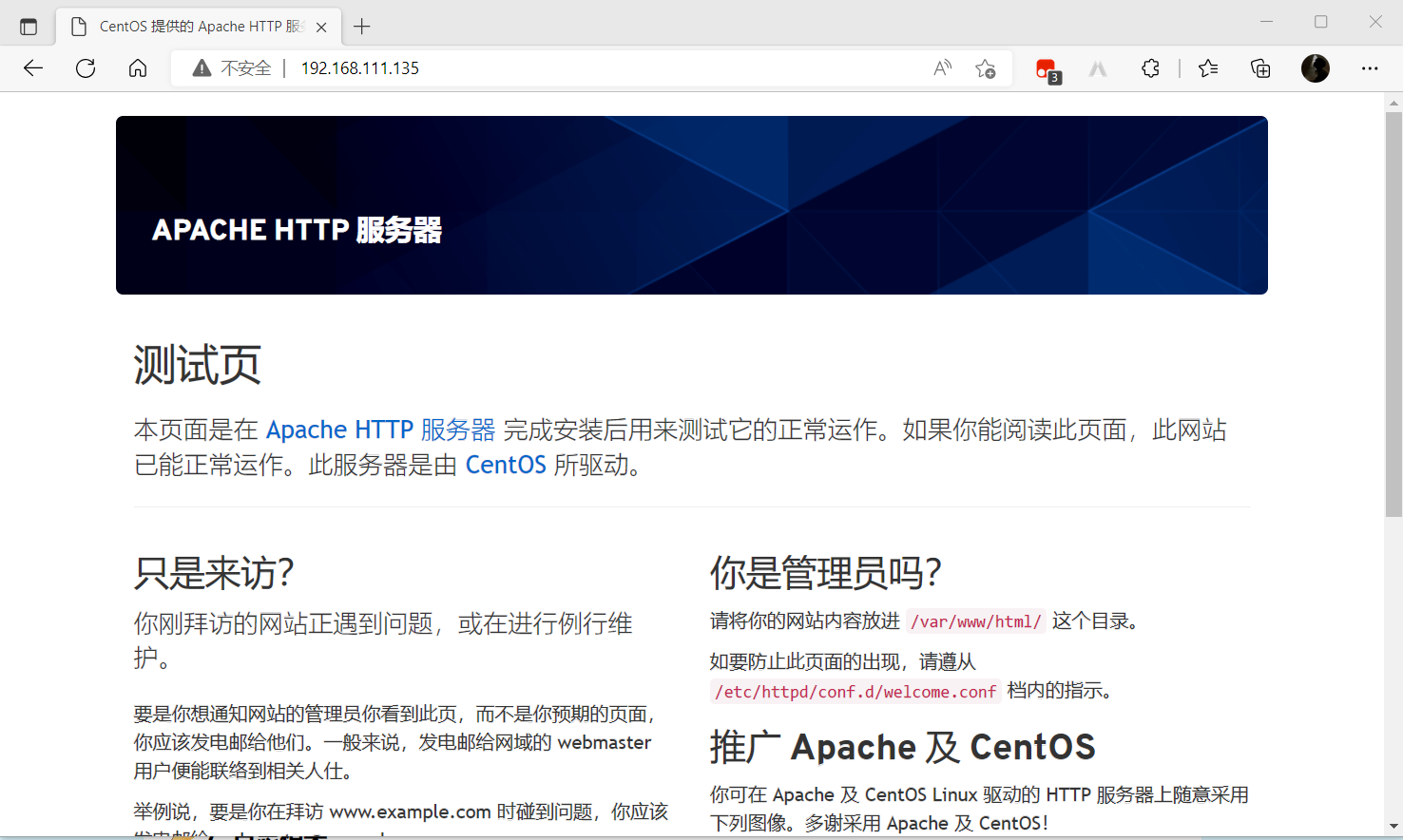
用瀏覽器輸入IP地址打開httpdde測試頁面
6.2 訪問控製法則
| 法則 | 功能 |
|---|---|
| Require all granted | 允許所有主機訪問 |
| Require all deny | 拒絕所有主機訪問 |
| Require ip IPADDR | 授權指定來源地址的主機訪問 |
| Require not ip IPADDR | 拒絕指定來源地址的主機訪問 |
| Require host HOSTNAME | 授權指定來源主機名的主機訪問 |
| Require not host HOSTNAME | 拒絕指定來源主機名的主機訪問 |
| IPADDR的類型 | HOSTNAME的類型 |
|---|---|
| IP:192.168.1.1 Network/mask:192.168.1.0/255.255.255.0 Network/Length:192.168.1.0/24 Net:192.168 | FQDN:特定主機的全名 DOMAIN:指定域內的所有主機 |
註意:httpd-2.4版本在配置文件加入Requirt才是預設是拒絕所有主機訪問的,所以安裝以後必須做顯示授權訪問
配置示例: 允許除了IP192.168.111.1以外的所有主機訪問
[root@localhost ~]# vim /etc/httpd/conf/httpd.conf
......
#
# Controls who can get stuff from this server.
#
Require all granted
</Directory>
<Directory "/var/www/html/Tanke">
<RequireAll>
Require not 192.168.111.1
Require all granted
</RequireAll>
</Directory>
#
# DirectoryIndex: sets the file that Apache will serve if a directory
# is requested.
#
......
[root@localhost ~]# httpd -t
AH00558: httpd: Could not reliably determine the server's fully qualified domain name, using localhost.localdomain. Set the 'ServerName' directive globally to suppress this message
Syntax OK
[root@localhost ~]# vim /etc/httpd/conf/httpd.conf //把#ServerName www.example.com:80前的#刪掉
#
# ServerName gives the name and port that the server uses to identify itself.
# This can often be determined automatically, but we recommend you specify
# it explicitly to prevent problems during startup.
#
# If your host doesn't have a registered DNS name, enter its IP address here.
#
#ServerName www.example.com:80
[root@localhost ~]# httpd -t
Syntax OK
6.3 虛擬主機
虛擬主機有三種:
- 相同IP不同埠
- 不同IP相同埠
- 相同IP相同埠不同功能變數名稱
httpd服務如何配置?
- 先在全局範圍內找*vhosts.conf文件
- 把*vhosts.conf文件複製到當前路徑中
相同IP不同埠
[root@localhost ~]# vim /etc/httpd/conf.d/httpd-vhosts.conf
......
<VirtualHost *:80>
DocumentRoot "/var/www/html/Tanke"
ServerName www.Tanke.com
ErrorLog "/var/log/httpd/www.Tanke1.com-error_log"
CustomLog "/var/log/httpd/www.Tanke1.com-access_log" common
</VirtualHost>
Listen 81
<VirtualHost *:81>
DocumentRoot "/var/www/html/Feiji"
ServerName www.Feiji.com
ErrorLog "/var/log/httpd/www.Feiji1.com-error_log"
CustomLog "/var/log/httpd/www.Feiji1.com-access_log" common
</VirtualHost>
......
[root@localhost ~]# httpd -t
Syntax OK
[root@localhost ~]# systemctl restart httpd
[root@localhost ~]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 *:80 *:*
LISTEN 0 128 *:81 *:*
LISTEN 0 128 [::]:22 [::]:*
不同IP相同埠
[root@localhost ~]# vim /etc/httpd/conf.d/httpd-vhosts.conf
......
<VirtualHost 192.168.111.135:80>
DocumentRoot "/var/www/html/Tanke"
ServerName www.Tanke.com
ErrorLog "/var/log/httpd/www.Tanke1.com-error_log"
CustomLog "/var/log/httpd/www.Tanke1.com-access_log" common
</VirtualHost>
<VirtualHost 192.168.111.136:80>
DocumentRoot "/var/www/html/Feiji"
ServerName www.Feiji.com
ErrorLog "/var/log/httpd/www.Feiji1.com-error_log"
CustomLog "/var/log/httpd/www.Feiji1.com-access_log" common
</VirtualHost>
......
[root@localhost ~]# httpd -t
Syntax OK
[root@localhost ~]# ip a //查看是否存在IP192.168.111.136
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
inet 192.168.111.135/24 brd 192.168.111.255 scope global dynamic noprefixroute ens160
valid_lft 1537sec preferred_lft 1537sec
inet6 fe80::3d5c:b9d6:55f:48e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@localhost ~]# ip addr add 192.168.111.136/24 dev ens160 //添加IP
[root@localhost ~]# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 00:0c:29:bb:22:82 brd ff:ff:ff:ff:ff:ff
inet 192.168.111.135/24 brd 192.168.111.255 scope global dynamic noprefixroute ens160
valid_lft 1463sec preferred_lft 1463sec
inet 192.168.111.136/24 scope global secondary ens160
valid_lft forever preferred_lft forever
inet6 fe80::3d5c:b9d6:55f:48e9/64 scope link noprefixroute
valid_lft forever preferred_lft forever
[root@localhost ~]# systemctl restart httpd //重啟httpd服務
相同IP相同埠不同功能變數名稱
[root@localhost ~]# vim /etc/httpd/conf.d/httpd-vhosts.conf
......
<VirtualHost *:80>
DocumentRoot "/var/www/html/Tanke"
ServerName www.Tanke.com
ErrorLog "/var/log/httpd/www.Tanke1.com-error_log"
CustomLog "/var/log/httpd/www.Tanke1.com-access_log" common
</VirtualHost>
<VirtualHost *:80>
DocumentRoot "/var/www/html/Feiji"
ServerName www.Feiji.com
ErrorLog "/var/log/httpd/www.Feiji1.com-error_log"
CustomLog "/var/log/httpd/www.Feiji1.com-access_log" common
</VirtualHost>
......
[root@localhost ~]# httpd -t
Syntax OK
[root@localhost ~]# systemctl restart httpd
主機名解析
Linux 和MAC系統中修改 /etc/host
windows主機名解析 在C:\windows\system32\drivers\etc\hosts找到文件無法修改,需要把文件拖到桌面修改,添加解析,再放回原位
7、配置https步驟
https(全稱:Hyper Text Transfer Protocol over SecureSocket Layer),是以安全為目標的 http 通道,在 http 的基礎上通過傳輸加密和身份認證保證了傳輸過程的安全性。
1. mod_ssl模塊
mod_ssl 模塊可以實現https加密認證。
//安裝mod_ssl模塊
[root@localhost ~]# dnf install -y mod_ssl
a).CACA生成一對密鑰
[root@localhost ~]# mkdir /etc/pki/CA
[root@localhost ~]# cd /etc/pki/CA
[root@localhost CA]# mkdir private
[root@localhost CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) #生成密鑰
Generating RSA private key, 2048 bit long modulus (2 primes)
....+++++
....................................................+++++
e is 65537 (0x010001)
[root@localhost CA]# openssl rsa -in private/cakey.pem -pubout #提取公鑰
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2vmOLM61l3syZOvzhO3O
9YzRUTF8IuGVv3F2ASWfUuvYTwq9Q7C5xxqaCOSR73iieQU9mkrtv98a8AoY/Oyd
9fehZbrMxgDUFL7skcRxhYpacYeLfhnDlMLCU73ilVa4K2ZSm4MNLJ6DKDzgOozu
wzOTNvvy7wrkHXyMDt4M0DOFc051sPwT4ncBQQKcHjDpi9A8iCAgWTbInNXvLjHg
FV2E4HxPlhgzNwf99D01JJVK8qZSeL+aj0gYlmpBvh60czHfi28nqp8qqZocmUXf
BDUHK27usf8s3Pmdi/9I1mwGYPOQoH/SzTC3ce9RTd2inzSaQCMdbZe7pmp4rPW2
rwIDAQAB
-----END PUBLIC KEY-----
b). CA生成自簽署證書
[root@localhost CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365 #生成自簽署證書
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:hb
Locality Name (eg, city) [Default City]:wh
Organization Name (eg, company) [Default Company Ltd]:zsl
Organizational Unit Name (eg, section) []:mxx
Common Name (eg, your name or your server's hostname) []:www.Tanke1.com
Email Address []:[email protected]
[root@localhost CA]# openssl x509 -text -in cacert.pem #讀出cacert.pem證書的內容
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
76:a0:c6:d4:e7:7a:4d:dc:21:1b:71:ba:25:8e:74:f3:1b:41:5b:2a
Signature Algorithm: sha256WithRSAEncryption
Issuer: C = cn, ST = hb, L = wh, O = zsl, OU = mxx, CN = www.Tanke1.com, emailAddress = [email protected]
Validity
Not Before: Jul 21 15:31:42 2022 GMT
Not After : Jul 21 15:31:42 2023 GMT
Subject: C = cn, ST = hb, L = wh, O = zsl, OU = mxx, CN = www.Tanke1.com, emailAddress = [email protected]
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:da:f9:8e:2c:ce:b5:97:7b:32:64:eb:f3:84:ed:
ce:f5:8c:d1:51:31:7c:22:e1:95:bf:71:76:01:25:
9f:52:eb:d8:4f:0a:bd:43:b0:b9:c7:1a:9a:08:e4:
91:ef:78:a2:79:05:3d:9a:4a:ed:bf:df:1a:f0:0a:
18:fc:ec:9d:f5:f7:a1:65:ba:cc:c6:00:d4:14:be:
ec:91:c4:71:85:8a:5a:71:87:8b:7e:19:c3:94:c2:
c2:53:bd:e2:95:56:b8:2b:66:52:9b:83:0d:2c:9e:
83:28:3c:e0:3a:8c:ee:c3:33:93:36:fb:f2:ef:0a:
e4:1d:7c:8c:0e:de:0c:d0:33:85:73:4e:75:b0:fc:
13:e2:77:01:41:02:9c:1e:30:e9:8b:d0:3c:88:20:
20:59:36:c8:9c:d5:ef:2e:31:e0:15:5d:84:e0:7c:
4f:96:18:33:37:07:fd:f4:3d:35:24:95:4a:f2:a6:
52:78:bf:9a:8f:48:18:96:6a:41:be:1e:b4:73:31:
df:8b:6f:27:aa:9f:2a:a9:9a:1c:99:45:df:04:35:
07:2b:6e:ee:b1:ff:2c:dc:f9:9d:8b:ff:48:d6:6c:
06:60:f3:90:a0:7f:d2:cd:30:b7:71:ef:51:4d:dd:
a2:9f:34:9a:40:23:1d:6d:97:bb:a6:6a:78:ac:f5:
b6:af
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Subject Key Identifier:
8F:33:2D:51:A9:40:12:AC:BA:56:09:42:A1:CC:38:E3:4C:2B:79:DF
X509v3 Authority Key Identifier:
keyid:8F:33:2D:51:A9:40:12:AC:BA:56:09:42:A1:CC:38:E3:4C:2B:79:DF
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
22:a1:8f:18:0d:53:a7:1f:59:41:cc:f1:b7:04:0e:9e:9c:23:
2b:ab:e7:47:d0:1c:39:de:e9:b4:99:72:44:ec:1d:40:7c:71:
73:d6:9c:98:d4:03:92:9a:5e:83:60:52:53:db:08:b9:e0:a0:
6b:98:7d:e5:13:0e:6a:3e:04:0f:0c:09:40:bb:1d:94:61:f8:
09:57:d2:d3:6e:32:b7:e5:02:ed:47:88:b7:3a:13:e9:a2:45:
0a:5d:b4:fd:40:96:fb:8f:0a:9d:8b:b4:a6:12:a4:14:b0:95:
ee:66:df:3f:3f:a1:bf:cd:e9:ad:7b:48:d5:67:11:4d:22:98:
4e:e3:b5:31:18:41:5d:ee:39:9f:ae:89:ba:69:76:11:3d:82:
37:09:02:69:3e:c2:26:c5:17:8e:97:a3:e4:10:bc:a2:8a:e3:
83:be:83:05:91:59:82:29:fa:34:d8:0d:31:7c:37:3e:28:48:
96:3c:04:38:d1:43:55:da:c5:de:65:ef:bb:3d:db:e8:66:50:
9f:7d:cf:77:4f:d9:55:c9:69:8e:c2:fa:ea:8f:8a:50:5a:c8:
da:b1:c5:50:60:fb:74:60:30:3c:01:ce:3e:c5:6c:f6:e2:04:
d1:ca:63:70:e8:84:90:b8:32:96:67:22:d2:7d:15:47:34:07:
c1:2a:47:70
-----BEGIN CERTIFICATE-----
MIIDzzCCAregAwIBAgIUdqDG1Od6TdwhG3G6JY508xtBWyowDQYJKoZIhvcNAQEL
BQAwdzELMAkGA1UEBhMCY24xCzAJBgNVBAgMAmhiMQswCQYDVQQHDAJ3aDEMMAoG
A1UECgwDenNsMQwwCgYDVQQLDANteHgxFzAVBgNVBAMMDnd3dy5UYW5rZTEuY29t
MRkwFwYJKoZIhvcNAQkBFgoxMjNAcXEuY29tMB4XDTIyMDcyMTE1MzE0MloXDTIz
MDcyMTE1MzE0MlowdzELMAkGA1UEBhMCY24xCzAJBgNVBAgMAmhiMQswCQYDVQQH
DAJ3aDEMMAoGA1UECgwDenNsMQwwCgYDVQQLDANteHgxFzAVBgNVBAMMDnd3dy5U
YW5rZTEuY29tMRkwFwYJKoZIhvcNAQkBFgoxMjNAcXEuY29tMIIBIjANBgkqhkiG
9w0BAQEFAAOCAQ8AMIIBCgKCAQEA2vmOLM61l3syZOvzhO3O9YzRUTF8IuGVv3F2
ASWfUuvYTwq9Q7C5xxqaCOSR73iieQU9mkrtv98a8AoY/Oyd9fehZbrMxgDUFL7s
kcRxhYpacYeLfhnDlMLCU73ilVa4K2ZSm4MNLJ6DKDzgOozuwzOTNvvy7wrkHXyM
Dt4M0DOFc051sPwT4ncBQQKcHjDpi9A8iCAgWTbInNXvLjHgFV2E4HxPlhgzNwf9
9D01JJVK8qZSeL+aj0gYlmpBvh60czHfi28nqp8qqZocmUXfBDUHK27usf8s3Pmd
i/9I1mwGYPOQoH/SzTC3ce9RTd2inzSaQCMdbZe7pmp4rPW2rwIDAQABo1MwUTAd
BgNVHQ4EFgQUjzMtUalAEqy6VglCocw440wred8wHwYDVR0jBBgwFoAUjzMtUalA
Eqy6VglCocw440wred8wDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0BAQsFAAOC
AQEAIqGPGA1Tpx9ZQczxtwQOnpwjK6vnR9AcOd7ptJlyROwdQHxxc9acmNQDkppe
g2BSU9sIueCga5h95RMOaj4EDwwJQLsdlGH4CVfS024yt+UC7UeItzoT6aJFCl20
/UCW+48KnYu0phKkFLCV7mbfPz+hv83prXtI1WcRTSKYTuO1MRhBXe45n66Juml2
ET2CNwkCaT7CJsUXjpej5BC8oorjg76DBZFZgin6NNgNMXw3PihIljwEONFDVdrF
3mXvuz3b6GZQn33Pd0/ZVclpjsL66o+KUFrI2rHFUGD7dGAwPAHOPsVs9uIE0cpj
cOiEkLgylmci0n0VRzQHwSpHcA==
-----END CERTIFICATE-----
[root@localhost CA]# mkdir certs newcerts crl
[root@localhost CA]# touch index.txt && echo 01 > serial
c).客戶端(例如httpd伺服器)生成密鑰
[root@localhost CA]# cd /etc/httpd && mkdir ssl && cd ssl
[root@localhost ssl]# (umask 077;openssl genrsa -out httpd.key 2048)
Generating RSA private key, 2048 bit long modulus (2 primes)
...+++++
...........................................................................+++++
e is 65537 (0x010001)
d).客戶端生成證書簽署請求
[root@localhost ssl]# openssl req -new -key httpd.key -days 365 -out httpd.csr
Ignoring -days; not generating a certificate
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:cn
State or Province Name (full name) []:hb
Locality Name (eg, city) [Default City]:wh
Organization Name (eg, company) [Default Company Ltd]:zsl
Organizational Unit Name (eg, section) []:mxx
Common Name (eg, your name or your server's hostname) []:www.Tanke1.com
Email Address []:[email protected]
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
e).CA簽署客戶端提交上來的證書
[root@localhost ssl]# openssl ca -in httpd.csr -out httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Jul 21 15:35:07 2022 GMT
Not After : Jul 21 15:35:07 2023 GMT
Subject:
countryName = cn
stateOrProvinceName = hb
organizationName = zsl
organizationalUnitName = mxx
commonName = www.Tanke1.com
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
EA:D9:52:5A:E7:84:C2:09:1A:15:5B:4D:F2:77:23:F0:1D:C1:F9:D0
X509v3 Authority Key Identifier:
keyid:8F:33:2D:51:A9:40:12:AC:BA:56:09:42:A1:CC:38:E3:4C:2B:79:DF
Certificate is to be certified until Jul 21 15:35:07 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
2. 在ssl.conf 中配置證書的位置
[root@localhost ~]# cd /etc/httpd/conf.d/
[root@localhost conf.d]# vim ssl.conf
......
//把#DocumentRoot "/var/www/html/Feiji"
#ServerName www.Feiji1.com:443#號刪除並指定其使用目錄路徑
<VirtualHost _default_:443>
# General setup for the virtual host, inherited from global configuration
DocumentRoot "/var/www/html/Feiji"
ServerName www.Feiji1.com:443
//配置證書的路徑
SSLCertificateFile /etc/httpd/ssl/httpd.crt
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you've both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
# ECC keys, when in use, can also be configured in parallel
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
......
3. 檢查配置文件是否有語法錯誤
[root@localhost conf.d]# httpd -t
Syntax OK
4. 重啟服務
[root@localhost conf.d]# systemctl restart httpd
[root@localhost conf.d]# ss -anlt
State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 *:443 *:*
LISTEN 0 128 *:80 *:*
LISTEN 0 128 [::]:22 [::]:*