本次是一個 Firewalld 的基礎操作實例,利用 Firewalld 圖形操作界面進行訪問控制操作。 ...

本次是一個Firewalld的基礎操作實例,利用Firewalld圖形操作界面進行訪問控制操作。
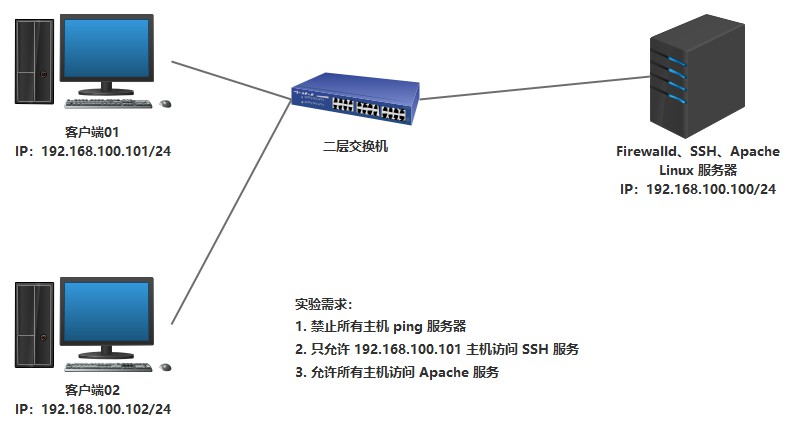
實驗拓撲
需求分析
首先拓撲涉及到兩個區域,這裡使用work和public區域,分別做相應的規則。
1.work區域禁止icmp,允許192.168.100.101訪問SSH服務,同時允許訪問Apache服務。
2.public區域禁止icmp,禁止SSH服務,允許訪問Apache服務。
分析方法:基於
Firewalld的數據處理流程,可參考上一篇博客。
操作過程
基礎準備
server安裝Apache服務,預設已存在SSH服務。
[root@server ~]# yum install -y httpd
[root@server ~]# echo "This is test page , all host can access" > /var/www/html/index.html
[root@server ~]# systemctl start httpd.service- 預設不關閉防火牆的情況下,可以
ping、ssh,不可以訪問apache。
[root@host01 ~]# ping -c4 192.168.100.100
PING 192.168.100.100 (192.168.100.100) 56(84) bytes of data.
64 bytes from 192.168.100.100: icmp_seq=1 ttl=64 time=0.573 ms
64 bytes from 192.168.100.100: icmp_seq=2 ttl=64 time=0.575 ms
64 bytes from 192.168.100.100: icmp_seq=3 ttl=64 time=1.15 ms
64 bytes from 192.168.100.100: icmp_seq=4 ttl=64 time=0.441 ms
--- 192.168.100.100 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3003ms
rtt min/avg/max/mdev = 0.441/0.686/1.156/0.277 ms[root@host01 ~]# curl 192.168.100.100
curl: (7) Failed connect to 192.168.100.100:80; No route to host[root@host01 ~]# ssh [email protected]
The authenticity of host '192.168.100.100 (192.168.100.100)' can't be established.
ECDSA key fingerprint is SHA256:5GGc1rmzWwjF+ozz/PPTyLO2s6NmFHSxbzCNsLazXhY.
ECDSA key fingerprint is MD5:0b:f5:62:d7:a4:1f:05:64:0b:7f:22:62:11:64:07:61.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.100.100' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Wed Oct 23 09:55:12 2019
[root@server ~]# logout
Connection to 192.168.100.100 closed.配置 Firewalld
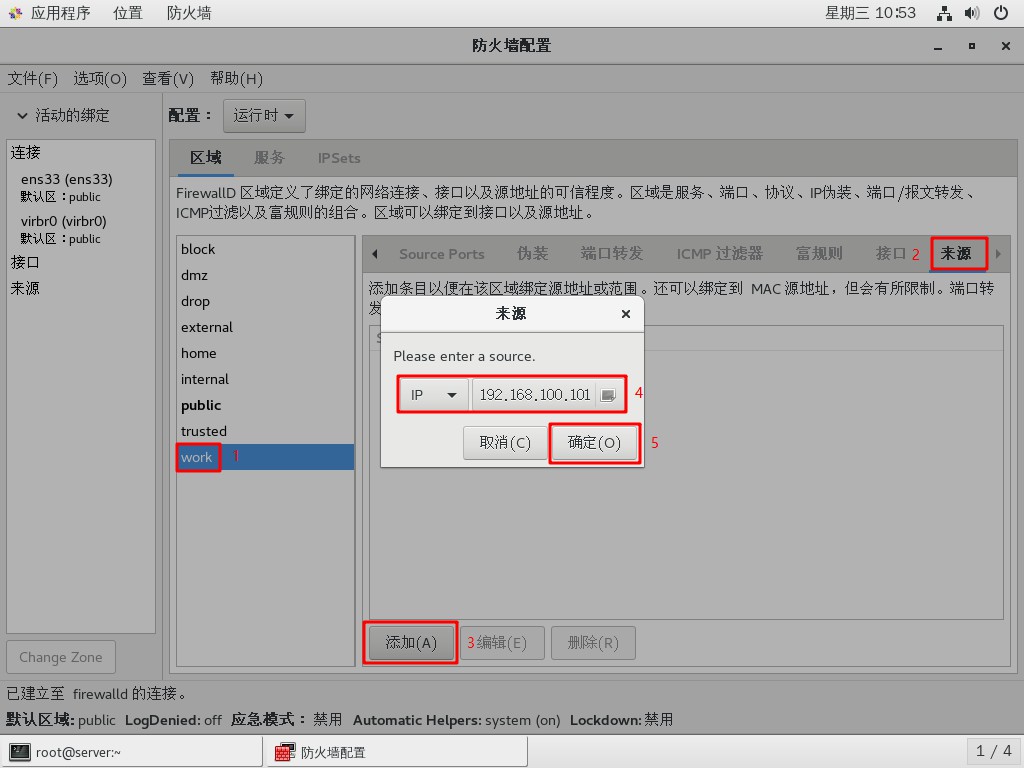
[root@server ~]# firewall-config- 給
work區域添加來源:192.168.100.101
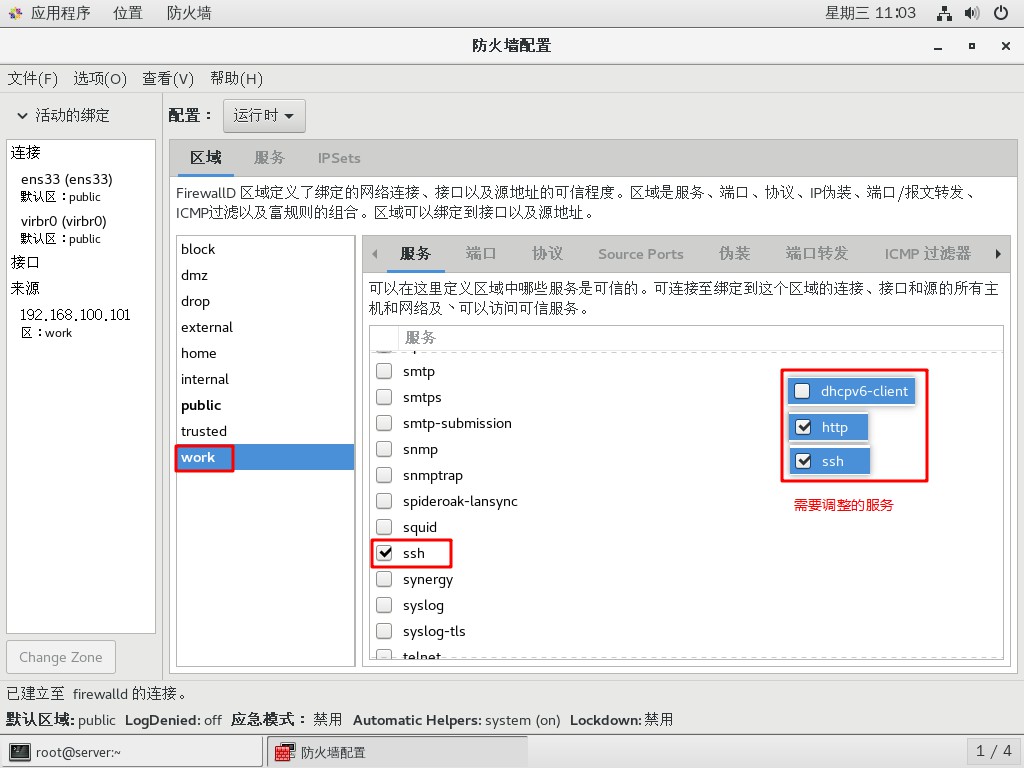
- 允許
work區域的http、ssh服務,禁止其他存在的服務
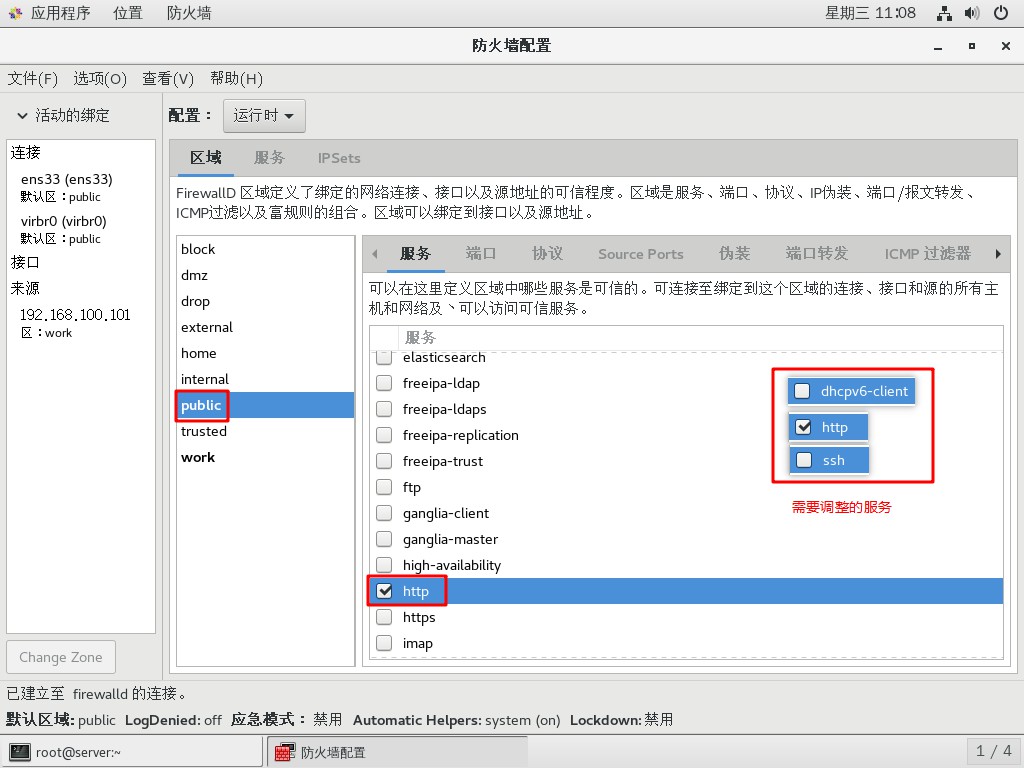
- 允許
public區域的http服務,禁止其他存在的服務
- 通過
ICMP過濾器禁止request請求,在兩個區域都做。
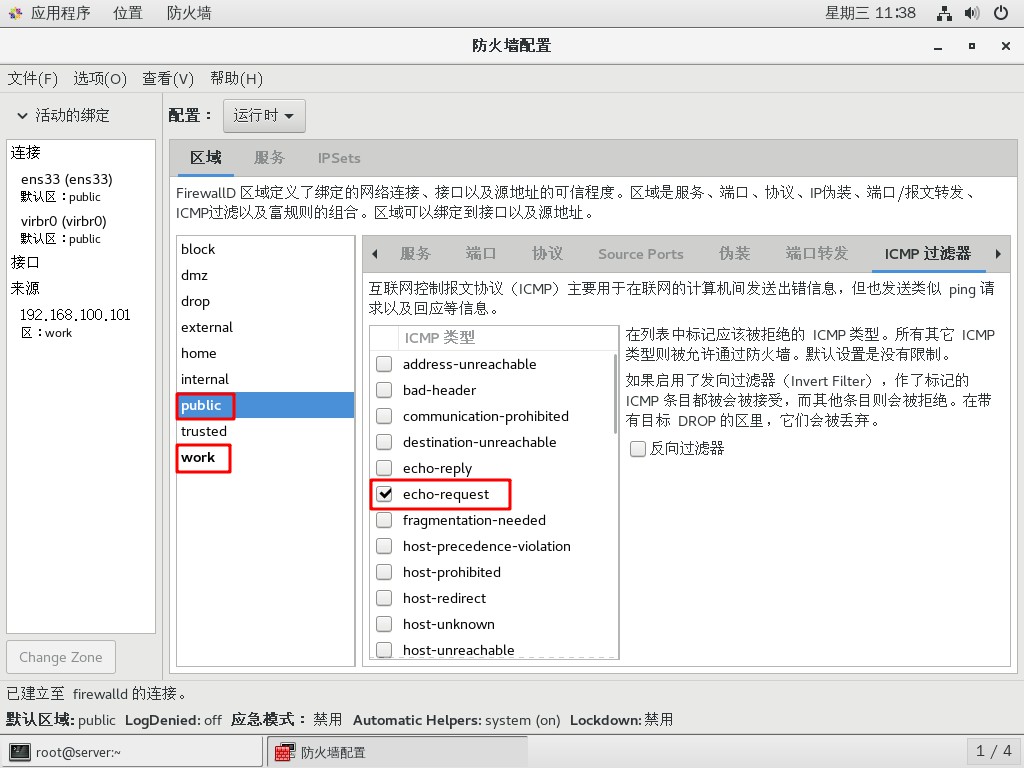
結果驗證
- 網站訪問
[root@host01 ~]# curl 192.168.100.100
This is test page , all host can access[root@host02 ~]# curl 192.168.100.100
This is test page , all host can accessSSH遠程
[root@host01 ~]# ssh [email protected]
[email protected]'s password:
Last login: Wed Oct 23 10:47:15 2019
[root@server ~]# logout
Connection to 192.168.100.100 closed.[root@host02 ~]# ssh [email protected]
ssh: connect to host 192.168.100.100 port 22: No route to hostping測試
[root@host01 ~]# ping -c4 192.168.100.100
PING 192.168.100.100 (192.168.100.100) 56(84) bytes of data.
From 192.168.100.100 icmp_seq=1 Destination Host Prohibited
From 192.168.100.100 icmp_seq=2 Destination Host Prohibited
From 192.168.100.100 icmp_seq=3 Destination Host Prohibited
From 192.168.100.100 icmp_seq=4 Destination Host Prohibited
--- 192.168.100.100 ping statistics ---
4 packets transmitted, 0 received, +4 errors, 100% packet loss, time 3001ms[root@host02 ~]# ping -c4 192.168.100.100
PING 192.168.100.100 (192.168.100.100) 56(84) bytes of data.
From 192.168.100.100 icmp_seq=1 Destination Host Prohibited
From 192.168.100.100 icmp_seq=2 Destination Host Prohibited
From 192.168.100.100 icmp_seq=3 Destination Host Prohibited
From 192.168.100.100 icmp_seq=4 Destination Host Prohibited
--- 192.168.100.100 ping statistics ---
4 packets transmitted, 0 received, +4 errors, 100% packet loss, time 3002ms永久配置
- 設置永久配置
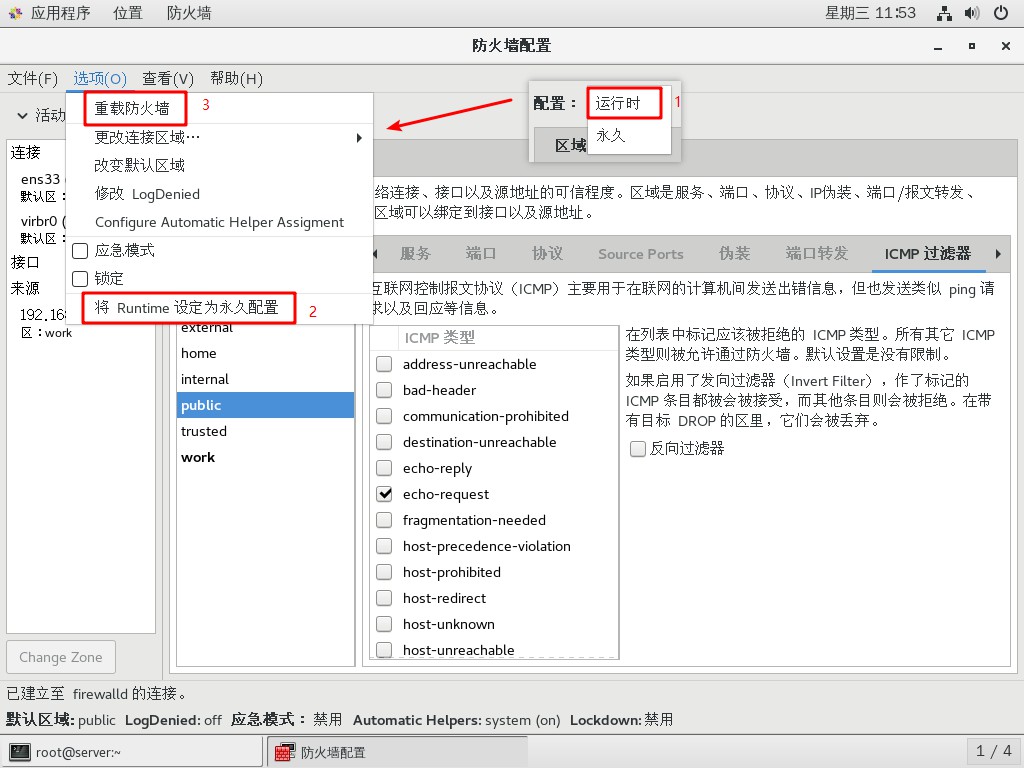
這裡配置的是
運行時配置,若要更改永久配置需點擊選項,首先將Runtime設定為永久配置,然後重載防火牆,直接重載防火牆會丟失運行時的配置。若是一開始就選擇的永久配置,則可以直接重載防火牆使配置生效。


